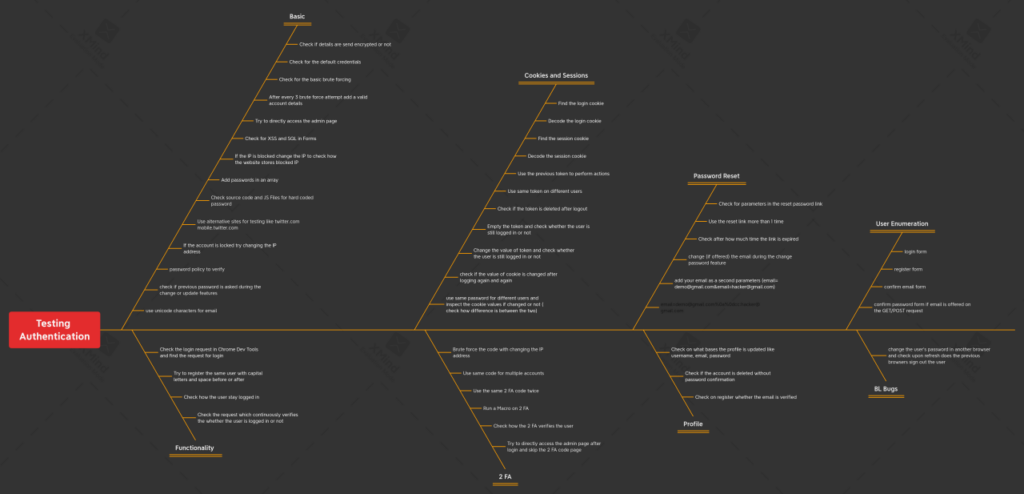
Common Authentication Bugs in Web Applications
1. Unencrypted Data Transmission
- The importance of encrypting data during transmission cannot be overstated. Unencrypted data can be intercepted by attackers, exposing sensitive information such as login credentials, personal details, and more.
- Implement Secure Sockets Layer (SSL) or Transport Layer Security (TLS) protocols to ensure data encryption. Failing to do so makes it easy for attackers to eavesdrop on communication between the client and the server.
2. Default Credentials
- Default credentials are often used during initial setup but should be changed immediately to prevent unauthorized access. Many web applications and devices ship with well-known default usernames and passwords.
- Attackers frequently attempt to gain access using default credentials, so changing them is a simple but critical security practice.
3. Brute Forcing
- Brute force attacks involve trying multiple combinations of usernames and passwords until the correct one is found. This is why strong password policies and account lockout mechanisms are crucial.
- Monitoring and detecting brute force attempts is essential to thwart such attacks. After a certain number of failed attempts, accounts should be temporarily locked.
4. Direct Access to Admin Page
- Allowing direct access to admin or privileged pages without proper authentication can lead to unauthorized control over the application’s backend.
- Implement strong authentication controls, such as requiring users to log in and perform proper authorization checks, before granting access to admin features.
5. XSS and SQL Injection in Forms
- Cross-site scripting (XSS) and SQL injection attacks are common methods of exploiting web application vulnerabilities. They often target input fields in forms.
- Input validation and output encoding are essential for preventing these attacks. Always sanitize and validate user inputs to protect against malicious payloads.
6. IP Blocking Bypass
- When an IP is blocked due to suspicious activity, attackers may attempt to bypass this restriction by changing their IP address.
- Implement rate-limiting and monitoring systems to identify and block repeated attempts from different IPs. Consider using Web Application Firewalls (WAFs) for added protection.
7. Hardcoded Passwords
- Hardcoded passwords within source code or JavaScript files are a significant security risk. Anyone with access to the code can discover these passwords.
- Avoid storing passwords in code and use secure authentication mechanisms, such as hashing and salting, to protect user credentials.
8. Alternative Site Testing
- Attackers may target subdomains or alternative versions of a website. It’s crucial to test and secure all web assets, not just the main site.
- Apply the same security practices and controls to all subdomains and sites associated with your web application.
9. Password Policy Manipulation
- Attackers may try to manipulate password policies to make it easier to guess or crack passwords. This includes reducing complexity requirements or increasing the maximum password length.
- Regularly review and update password policies, and ensure they align with best practices for password security.
10. Unicode Character Exploitation
- Using Unicode characters in email addresses can lead to issues with email validation. Attackers might exploit this by using specially crafted Unicode characters to create lookalike email addresses.
- Implement thorough email validation routines to ensure that email addresses conform to the expected format and don’t contain malicious characters.
11. Capital Letters and Whitespace in Usernames
- Varying capitalization and adding whitespace to usernames can confuse authentication systems and lead to security vulnerabilities.
- Normalize usernames by converting them to lowercase and removing whitespace before storing and comparing them during authentication.
12. Persistent Login
- Persistent login (also known as “Remember Me” functionality) can expose users to long-term risks if not implemented securely.
- Implement token-based solutions for persistent login and ensure tokens are securely stored and invalidated upon user logout or password change.
13. Session Tokens
- Session cookies or tokens are critical components of user authentication. Attackers may attempt to steal, manipulate, or replay these tokens.
- Implement secure session management practices, including token expiration and secure token storage.
14. Finding and Decoding Login Cookies
- Understanding how login cookies work is essential for both developers and attackers. Attackers may try to decode or manipulate these cookies.
- Use strong encryption and hashing algorithms for login cookies to make them resistant to tampering.
15. Session Cookie Analysis
- Session cookies store user session information, and attackers may try to exploit them to impersonate legitimate users.
- Use secure cookies, regenerate session IDs upon login, and employ proper session management to mitigate these risks.
16. Token Manipulation
- Attackers might attempt to manipulate authentication tokens to gain unauthorized access.
- Implement strong token validation and validation checks to detect and prevent token manipulation.
17. Token Deletion and Modification
- Deleting or modifying tokens can lead to unauthorized access. Ensure tokens are properly invalidated upon logout or any other event that requires session termination.
- Regularly audit token management to identify potential issues.
18. Cross-User Token Usage
- Reusing the same token for multiple users can lead to security breaches and session hijacking.
- Implement token binding mechanisms to ensure tokens are unique to each user session.
19. Cookie Value Alteration
- Modifying cookie values can potentially grant attackers unauthorized access.
- Implement proper input validation and consider using HttpOnly and Secure flags for cookies to enhance security.
20. Cookie Value Comparison
- Cookie values should remain consistent during a user’s session. Changes may indicate a security issue.
- Implement strict validation checks for cookie values and consider implementing token-based authentication for enhanced security.
21. IP Address Brute Forcing
- Attackers may attempt brute force attacks by changing their IP address.
- Implement rate limiting and IP blocking to deter brute force attacks and monitor for suspicious patterns in login attempts.
22. Two-Factor Authentication (2FA)
- Two-factor authentication is a powerful security feature, but it can have vulnerabilities if not implemented correctly.
- Ensure the 2FA process is robust and resistant to various attacks, including code reuse and bypass attempts.
23. Direct Access to Admin Page After Login
- Allowing direct access to admin pages after login without proper 2FA validation can compromise security.
- Implement 2FA checks for all privileged actions, even after the initial login.
24. Reset Password Link Parameters
- Password reset links should include secure parameters to prevent tampering or abuse.
- Include time-limited and single-use tokens in reset links and validate them before allowing password changes.
25. Multiple Use of Reset Links
- Reset links should be single-use to prevent attackers from repeatedly changing a user’s password.
- Implement a mechanism to invalidate reset links after they’ve been used.
26. Link Expiration
- Password reset links should expire after a set time to enhance security.
- Set a reasonable expiration period and clearly communicate it to users during the password reset process.
27. Email Address Manipulation
- Attackers may try to manipulate email addresses during the password change process to gain unauthorized access.
- Validate email addresses thoroughly and implement additional security checks, such as reconfirming the email before allowing password changes.
28. Profile Updates
- User profile updates should be secure and subject to proper authentication and authorization checks.
- Validate and sanitize user inputs during profile updates and enforce appropriate access controls.
29. Account Deletion Security
- Deleting accounts should require proper authentication to prevent unauthorized removal of user data.
- Implement multi-factor authentication or email confirmation before allowing account deletion.
30. User Enumeration
- User enumeration occurs when attackers can determine valid usernames or email addresses through login, registration, or password reset processes.
- Implement generic error messages to avoid leaking information about valid users.
31. Account Verification
- Require email verification during the registration process to ensure that users provide valid email addresses.
- Implement a time limit for email verification to prevent abuse.
32. Profile Updates (Again)
- Secure user profile updates are crucial to maintaining data integrity and preventing unauthorized changes.
- Reiterate the importance of proper validation and access controls during profile updates.
33. Email Verification Impact on Other Browsers
- Email verification should be enforced consistently across different browsers to maintain security.
- Test email verification thoroughly to ensure it functions correctly on various platforms.